The Latest Riverbed News
Product and Solution Information, Press Releases, Announcements
Protecting End Users in an SD-WAN World
February 03, 2020 By BlueAlly

When it comes to an SD-WAN deployment we tend to spend a lot of time thinking about connectivity, reachability, protocols, traffic steering and so on. One area that we sometimes overlook is SD-WAN security. It’s easy to do. Take for example a network deployment with several MPLS branches. All traffic is backhauled to the data center and then pushed through our high-end firewalls. The security group handles the firewalls. The infrastructure group handles the WAN and routing. Everyone has their own lane to stay in. Life is okay. But now the infrastructure group is talking about SD-WAN and how it’s going to help save money. The plan is to replace our WAN-edge routers with Riverbed’s SteelConnect EX SDWAN solution. From that replacement, we gain the ability to move to multiple lower-cost Internet circuits, perform application identification and path-quality-path-selection. Our routing protocols are compatible. All the bases seem to be covered, or are they?
Does SD-WAN deployment require backhaul?
Once an SD-WAN deployment is in place and Internet circuits are in use we look at how we can improve performance for our end-users. Backhauling user data over an Internet-based VPN can add latency and cause the end-user to experience delays.
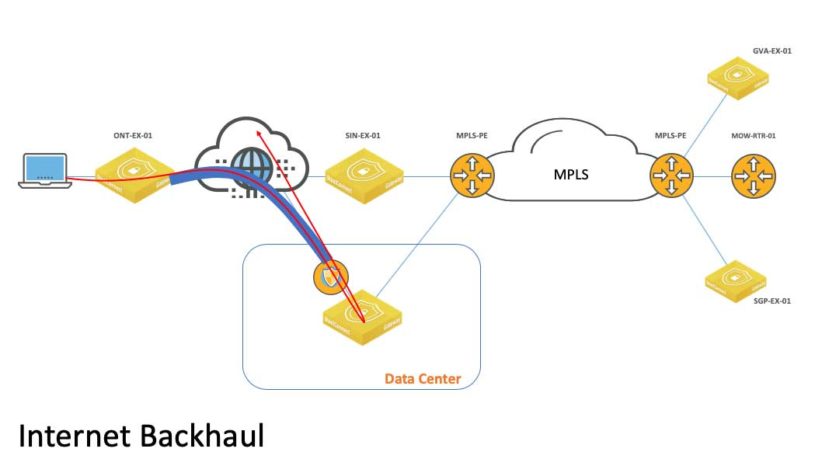
This obviously impacts the human experience and we need to avoid that. This happens to be one of the benefits of an SDWAN deployment. With Internet circuits deployed at each branch, we can shave some of that latency by sending select traffic direct to the Internet. An example of the type of traffic that is normally sent “direct-to-net” as it’s referred to, is Microsoft Office 365, Salesforce, or Workday bound traffic.
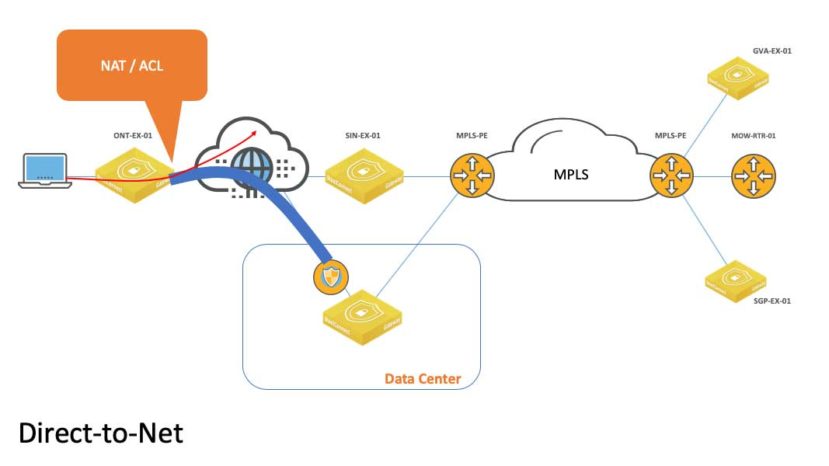
What this translates to is the WAN-edge device now being required to perform Network Address Translation (NAT) and at minimum a Stateful Firewall service. This allows outbound sessions to be tracked in a state table. Inbound traffic is referenced against that table to determine if it is a valid reply to an existing outbound connection. If it is, the traffic can pass. If it’s not, the traffic is discarded. The good news is that the Riverbed SteelConnect EX SDWAN solution provides this capability, and a whole lot more.
SteelConnect EX SD-WAN security capabilities
The SteelConnect EX offers a rich security feature set that’s licensed-based. There are three license levels:
- Secure SD-WAN Essentials, includes Stateful and Next-generation firewall (NGFW) capabilities
- Secure SD-WAN Standard, also includes Stateful and NGFW capabilities
- Secure SD-WAN Advanced, includes Stateful, NGFW, as well as Unified Threat Management features.
We will discuss these capabilities in the following sections.
Stateful Firewall
The stateful firewall provides a mechanism to enable full visibility of the traffic that traverses through the firewall and also enforces very fine grain access control on the traffic. To begin making use of this capability you must classify traffic. This is the process of identifying and separating traffic in a manner that makes it identifiable to the firewall service. To classify the traffic, the stateful firewall verifies its destination port and then tracks the state of the traffic. SteelConnect EX monitors every interaction of each connection until the session is closed.
The stateful firewall grants or rejects access based not only on port and protocol but also on the history of the packet in the state table. When the SteelConnect EX stateful firewall receives a packet, first it checks the state table for an established connection or for a request for the incoming packet from an internal host. For example, when an internal host establishes an HTTP session to an external server, it begins by establishing a TCP session. This is the process of SYN, SYN-ACK, ACK. Until that three-way-handshake is completed the flow of packets is not considered a “session.” Therefore, when a TCP SYN is sent from an internal host, outbound, this is entered into the state table. The returning SYN-ACK is verified against the information in the state table. If nothing is found then the packet’s access is subject to the access policy rule.
An access policy rule gives us a way to decide if traffic can pass even if it does not match an entry in the state table. An example of this would be ICMP traffic. ICMP is not a stateful protocol, so therefore we could say in an access policy rule that all ICMP traffic inbound is allowed, regardless of a state entry or not. Most of the time an access policy is used to allow inbound access to services such as Web and FTP servers. This is not very common for the branch office.
NGFW
The Next-generation firewall (NGFW) is a robust security module that has the intelligence to distinguish different types of traffic. Recall that the Stateful firewall made use of ports, protocols, and IP addresses to identify traffic and create an entry in the state table. The NGFW provides network protection beyond the protection based on ports, protocols, IP addresses. In addition to traditional firewall capabilities, the NGFW includes filtering functions such as an application firewall, an intrusion prevention system (IPS), TLS/SSL encrypted traffic inspection, website filtering, and QoS/bandwidth management.
These features can all be enabled, based on your license, and applied to a group of devices. It’s expected to see some type of performance impact when implementing these features, however, this should be a nominal impact and you should weigh out the need for the feature versus the impact prior to rolling the feature out to a large number of sites. The way I like to look at these features is like a toolbox filled with specialty tools. Not every situation requires the use of a hammer, so figure out what tool you need for your situation and implement it accordingly.
Unified Threat Management
SteelConnect EX includes Unified Threat Management (UTM) capabilities, which can be turned on by configuring the threat profiles in the NGFW policy rules. This means that UTM requires the use of the NGFW first.
The following threat profiles are supported:
- Antivirus
- Vulnerability (IDS/IPS)
SteelConnect EX has a built-in antivirus engine. This engine will scan live traffic looking for threats. To accomplish this, the antivirus engine waits till the last byte of the file is received before processing the entire file at runtime. You will need to configure at least one antivirus profile to enable the scanning of files for viruses.
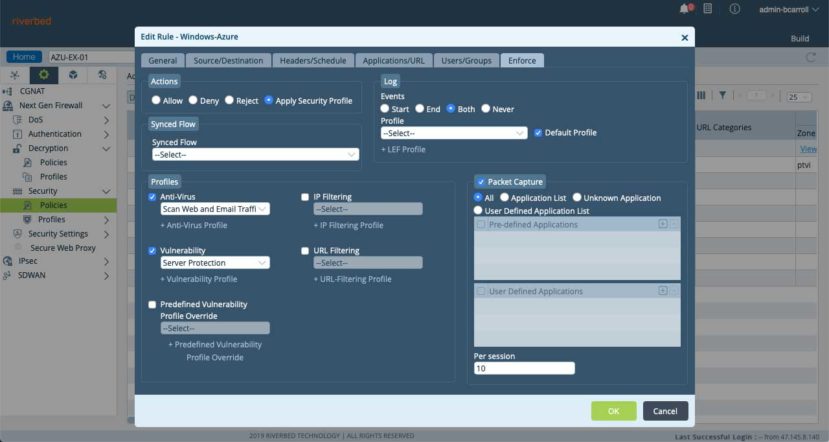
To enable and enforce and antivirus profile a NGFW policy rule must be configured. When configured, the antivirus profile is applicable to all traffic that matches the security policy rule. Taking things a step further, what you tell the antivirus profile to do, is extract files from certain types of traffic. This could include HTTP, FTP, and common email protocols. As you might have guessed, the protocols the antivirus engine extracts files from are commonly used to transmit these types of threats.
When a file is extracted from one of these protocols it is buffered, forwarded to the destination (with the exception of the last packet), and scanned. If a virus is found the profile action is applied, otherwise the last packet is sent.
An antivirus profile supports the following enforcement actions:
- Alert—Alerts the user when a virus is found. Virus information is stored in a log file.
- Allow— The antivirus profile does not scan the file. It just allows it.
- Deny— The antivirus profile aborts the flow on which the virus file is received.
- Reject— Both client and server connection is reset.
Final thoughts
In this article, we’ve discussed three levels of SD-WAN security capability featured in the Riverbed SteelConnect EX SD-WAN solution. Knowing that these features are available can help make the determination of how branch traffic is handled. If the decision is to backhaul all Internet-bound traffic to the data center, then there won’t be much of a need to employ these advanced security features, outside of basic protection for a device. If the decision is to enhance the user experience by sending specific traffic “direct-to-net” then these features should certainly be discussed and the degree to which they are implemented will need to be determined. All-in-all the SteelConnect EX solution provides a proper degree of protection for branch traffic when Internet uplinks are made available.
But what about performance? A decision to backhaul will provide some benefits but more is involved in ensuring the user experience is the best it can be. For example, Microsoft services are regional and users may still experience less than ideal performance. The same is true for other SaaS offerings, largely due to the location of the services. For this, I urge you to have a look at the Riverbed SaaS Accelerator service. SaaS Accelerator combined with SteelConnect EX provides the highest level of WAN connectivity, branch security, and end-user performance, focused on enhancing user productivity.
